Password Strength Meter
Check your password security instantly with our advanced strength analyzer tool
Check Your Password Strength
Password Security Tips:
- Use a minimum of 12 characters for better security
- Combine uppercase and lowercase letters
- Include numbers and special characters like !@#$%^&*
- Avoid common words, names, and personal information
- Consider using a memorable passphrase instead of a single word
- Never reuse passwords across multiple accounts
Understanding Password Strength Analysis
A password strength analyzer is a specialized security tool designed to evaluate the effectiveness of user-created passwords by assessing multiple factors that contribute to their resilience against unauthorized access attempts. These sophisticated tools provide real-time feedback during password creation, helping users understand the security level of their chosen credentials before finalizing them.
Key Password Security Factors
Contemporary password strength assessment tools extend beyond basic character counting. They evaluate multiple dimensions of password security including length, character diversity, unpredictability, and uniqueness against known compromised credential databases. Advanced analyzers incorporate sophisticated algorithms that calculate entropy (a mathematical measure of randomness), check against known breached password databases, and evaluate resistance to common hacking techniques like dictionary attacks and brute force attempts.
The most effective password strength tools provide not just a security rating but also actionable guidance to help users improve weak credentials. This educational component is crucial in helping users understand why certain password choices are vulnerable and how to create stronger alternatives. By offering real-time guidance during password creation, these tools play a vital role in enhancing overall cybersecurity awareness and practices across digital platforms.
Utilizing Password Strength Assessment
Using a password strength evaluation tool is straightforward, but understanding how to interpret its feedback is essential for improving your credential security. Begin by entering your password into the designated input field. As you type, the analyzer will assess your password in real-time and provide immediate feedback through visual indicators and strength classifications.
Step 1: Enter Your Password
Type your password into the designated field. The analyzer will evaluate it character by character, updating its assessment as you type. For accurate results, enter your complete password rather than a portion of it.
Step 2: Review the Feedback
Examine the strength meter's visual feedback (color-coded bar) and textual assessment. Common strength levels include Very Weak, Weak, Medium, Strong, and Very Strong, each associated with specific colors.
Step 3: Check Security Criteria
Review the checklist of security requirements to see which criteria your password meets and which it fails. Common requirements include minimum length, use of different character types, and avoidance of common patterns.
Step 4: Enhance Your Password
Based on the feedback, modify your password to meet more security criteria. The analyzer updates in real-time, allowing you to see the impact of each change immediately and create the strongest possible credential.
Users who follow analyzer suggestions create significantly stronger credentials
Strong passwords resist hacking attempts much longer than weak ones
Your password is analyzed locally and never leaves your device
For optimal security, continue refining your password until it reaches the highest strength rating. Reputable password strength tools evaluate credentials locally in your browser without transmitting them over the internet, ensuring your potential passwords remain private during the evaluation process.
Advantages of Password Strength Evaluation
Password strength assessment tools offer significant advantages for both individual users and organizations by enhancing security awareness and promoting better credential practices. These tools serve as educational resources that help users understand what constitutes a strong password, bridging the gap between technical security requirements and user behavior.
For organizations, implementing password strength analysis significantly reduces the risk of security breaches caused by weak credentials. By enforcing stronger password policies at the point of creation, these tools prevent users from setting easily compromised passwords that could endanger entire systems. This proactive security approach saves substantial resources that might otherwise be spent on breach mitigation and recovery.
Password strength tools also help organizations comply with industry regulations and security standards that mandate robust authentication practices. By providing real-time feedback, these tools create a seamless user experience that educates without frustrating users, striking a balance between security and usability that is crucial for widespread adoption of good credential hygiene practices.
Password Analysis Methodology
Password strength assessment tools employ sophisticated algorithms to evaluate the security level of credentials. At their core, these systems analyze multiple factors that contribute to a password's resistance against common attack methods. The evaluation process typically considers length, character diversity, unpredictability, and uniqueness against known compromised credentials.
Advanced password strength tools utilize entropy calculations to measure the randomness and unpredictability of passwords. Entropy, measured in bits, quantifies the number of guesses an attacker would need to make to correctly identify a password. Higher entropy values indicate stronger credentials. Modern analyzers also incorporate checks against databases of known compromised passwords, ensuring users don't select credentials that have already been exposed in previous data breaches.
Some sophisticated password strength tools employ machine learning algorithms trained on millions of real-world credentials and breach data. These systems can identify patterns and characteristics that make passwords vulnerable, even if they meet traditional complexity requirements. By analyzing factors like keyboard walk patterns, dictionary words with character substitutions, and contextual information, these advanced systems provide more accurate assessments of password security.
The most comprehensive password analysis tools go beyond simple strength ratings to provide estimated "time-to-crack" metrics. These estimates calculate how long it would take an attacker using modern hardware to brute force the password. This tangible feedback helps users understand the practical security implications of their password choices and motivates them to create stronger credentials.
Explanation of How the Generator Works
The RP Generator UK utilizes advanced cryptographic algorithms to create truly random passwords that are virtually impossible to predict or replicate. Our system combines multiple entropy sources including system timings, hardware-based random number generators, and atmospheric noise to ensure maximum unpredictability.
When you request a password, our algorithm first gathers entropy from these multiple sources, creating a seed value with extremely high randomness. This seed then initializes a cryptographically secure pseudorandom number generator (CSPRNG) which produces a sequence of random characters according to your specified parameters.
The generator supports various character sets including uppercase letters, lowercase letters, numbers, and special symbols. You can customize the length and complexity based on your security requirements. Each password is generated in real-time and displayed only once, ensuring it remains secure throughout the process.
Our system employs industry-standard security practices including salting and hashing during the generation process to further enhance security. The entire operation happens locally in your browser, meaning no password data is transmitted over the internet, providing an additional layer of protection against interception.
Does It Store Data? (It Should Not)
No Storage
Local Processing
Client-Side Only
RP Generator UK is designed with privacy as a fundamental principle. We do not store any passwords, user data, or generation parameters on our servers or in any persistent storage. The entire password generation process occurs locally within your web browser using JavaScript, meaning no data is transmitted to external servers.
This client-side approach ensures that your generated passwords never leave your device, eliminating the risk of interception during transmission or unauthorized access to stored password databases. Once you close the browser tab or refresh the page, all traces of the generated passwords are completely erased from memory.
We have implemented a strict no-logging policy for our application. We do not track user sessions, collect analytics on password generation, or maintain any records of user activity. The application functions as a self-contained tool that operates entirely within the security boundaries of your local environment.
For additional peace of mind, our code is open for inspection, allowing security experts to verify that no data collection or transmission occurs. We believe that transparency is crucial for building trust in security tools, especially those dealing with sensitive information like passwords.
Security Information
RP Generator UK employs multiple layers of security to ensure the passwords generated are cryptographically strong and resistant to various attack vectors. Our system uses a combination of hardware-based and software-based entropy sources to create truly random seeds for password generation.
The core of our security model relies on the Web Cryptography API, which provides access to cryptographically strong random number generation capabilities built into modern browsers. This API taps into underlying operating system entropy sources, ensuring high-quality randomness that meets or exceeds industry standards.
We've implemented additional security measures including timing attack protections, which prevent side-channel analysis that could potentially reveal information about the generation process. The application also includes safeguards against common web vulnerabilities such as cross-site scripting (XSS) and cross-site request forgery (CSRF).
All cryptographic operations are performed in isolated execution environments with strict access controls. The application undergoes regular security audits by independent third-party experts to identify and address potential vulnerabilities. We maintain a responsible disclosure policy and encourage security researchers to report any issues they discover.
User Instructions
Click Generate
Wait for Processing
Copy Password
Using RP Generator UK is straightforward and requires no technical expertise. Simply click the "Generate Password" button located at the bottom of this page. The system will immediately begin creating a secure random password based on default parameters (12 characters including uppercase, lowercase, numbers, and symbols).
During the generation process, you will see an animated loader indicating that the system is working. This typically takes only a few seconds as the algorithm gathers sufficient entropy and processes the random data. Please do not refresh the page or navigate away during this process to ensure successful password generation.
Once complete, your new secure password will appear in the display area below the button. You can then select and copy the password to your clipboard by highlighting it and using Ctrl+C (or Cmd+C on Mac) or right-clicking and selecting "Copy". We recommend pasting the password directly into your target application's password field.
For advanced users, we plan to introduce customization options in future updates, allowing you to specify password length, character sets, and exclusion of similar-looking characters. These options will provide greater flexibility for meeting specific password policy requirements while maintaining security standards.
User Warnings and Best Practices
While RP Generator UK creates highly secure passwords, their effectiveness depends on proper handling and storage. Always ensure you're using a secure connection (HTTPS) when accessing this tool and verify that the website address is correct to avoid phishing attempts.
We strongly recommend using a password manager to store your generated passwords securely. Password managers encrypt your credentials and often include features like automatic form filling, which reduces the risk of keyloggers capturing your passwords as you type them.
Avoid reusing passwords across multiple accounts. If one service experiences a data breach, reused passwords could compromise your other accounts. Generate a unique password for each service or account you use, regardless of its perceived importance.
Be cautious when generating passwords on public or shared computers, as malware or keyloggers might be present. Always ensure you're using updated antivirus software and a secure browser. Consider using private/incognito browsing mode when generating passwords on computers you don't fully control.
Generating secure password...
Common Questions About Password Security
A secure credential combines sufficient length (minimum 12 characters), character diversity (uppercase, lowercase, numbers, symbols), unpredictability (avoiding dictionary words and patterns), and uniqueness (not reused across accounts). The most secure credentials are actually passphrases - sequences of random words that are memorable but resistant to cracking attempts.
The reliability of password strength evaluations varies depending on their algorithms. Basic tools that only check length and character types are less accurate than advanced systems that evaluate entropy, check against breach databases, and use machine learning. The most sophisticated analyzers provide highly accurate assessments that closely reflect real-world vulnerability.
Reputable online password strength tools operate client-side in your browser, meaning your credentials never leave your device. Look for tools that explicitly state they don't transmit passwords over the internet. For maximum security, use open-source tools that you can run locally on your computer.
Different password strength tools use different algorithms and weighting systems for various factors. Some may prioritize length over complexity, while others focus on uniqueness and resistance to dictionary attacks. The specific criteria and thresholds for each strength level also vary between tools.
Current security best practices recommend changing passwords only when there's evidence of compromise, rather than on a fixed schedule. However, you should immediately change credentials that are weak, reused across multiple sites, or potentially exposed in data breaches. Using unique, strong passwords for each account is more important than frequent rotation.
Password managers offer significant security advantages for most users. They generate and store truly random, unique credentials for each account, eliminating the human tendency to create predictable patterns or reuse passwords. For individuals managing numerous accounts, password managers provide both stronger security and greater convenience.
Two-factor authentication (2FA) adds an extra security layer beyond your password, typically requiring a temporary code from your phone or a security key. Even if your password is compromised, attackers can't access your account without this second factor. Security experts strongly recommend enabling 2FA on all important accounts, especially email, financial services, and social media.
Attackers use various techniques including dictionary attacks (trying common words), brute force attacks (trying all possible combinations), credential stuffing (trying username/password pairs from previous breaches), and social engineering. Advanced attackers use specialized hardware that can test billions of passwords per second, making strong credential practices essential.
If your credential appears in a known breach, immediately change it for all accounts where you've used that password or similar variations. Enable two-factor authentication where available, and consider using a password manager to generate and store unique, strong credentials for each account going forward.
Security experts recommend a minimum of 12 characters for most accounts, with 16 or more characters for high-security accounts like email and financial services. Longer credentials are exponentially harder to crack. A 12-character password with diverse characters would take centuries to crack with current technology, while an 8-character password could be compromised in hours or days.
SEO Tools Dashboard
Password & Key Generators
12 toolsIP Address & Network Tools
6 toolsName Generators
5 toolsPhone Number Generators
3 toolsAI Content Generators
2 toolsOur Latest Blogs

10 Steps to Improve Your Password Protection
Introduction: In today’s digital world, “password protection” is no longer just a technical term used by IT experts. It is something every internet user must
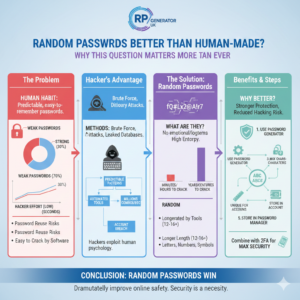
Are Random Passwords Better Than Human-Made?
Introduction: Why This Question Matters More Than Ever Have you ever created a password and felt confident because it included your name, a birthday, or

How Long Should a Password Be?
Have you ever found yourself staring at a computer screen, trying to think of a secret code, and wondered how long a password can be

What Is a Strong Password?
Introduction: Why This Question Matters More Than Ever What is a strong password? This question sounds simple, yet it quietly protects your emails, bank accounts,
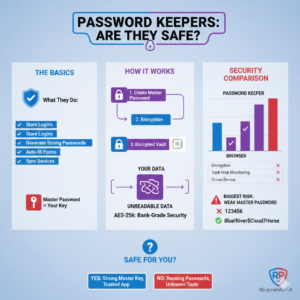
Are password keepers safe?
We will explain how password keepers work, how safe they really are, real-life stories, step-by-step guides, risks, benefits, and how to choose the right one.
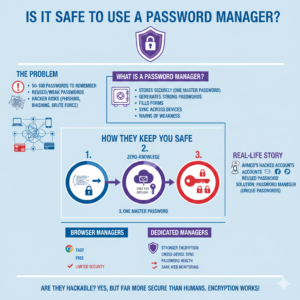
Is It Safe to Use a Password Manager?
In today’s online world, passwords are everywhere. Email, social media, banking, shopping, work tools—everything asks for a password. Now imagine trying to remember 50–100 different
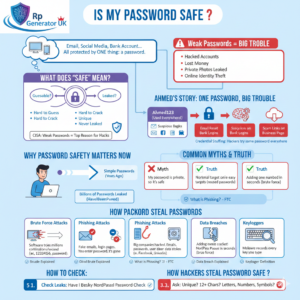
Is My Password Safe?
Have you ever logged into your email, social media, or bank account and suddenly wondered,“Is my password safe?” If yes, you are already one step
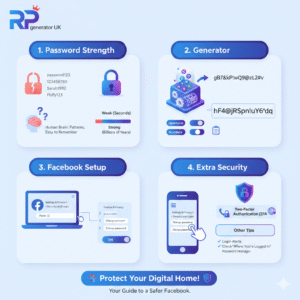
How to Use a Random Password Generator for Facebook?
Introduction: Imagine your Facebook account is your house. Inside, you have all your photos, your conversations with friends, and memories you’ve shared over the years.
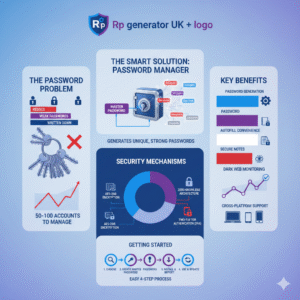
Why is a password manager one of the smartest things you buy?
Introduction: Imagine you have a hundred different doors in your life, and each one needs a unique key. Your front door, your car, your office,
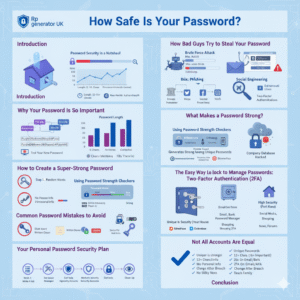
How Safe Is Your Password?
Introduction: Imagine your front door key. You wouldn’t make it simple, like a paperclip that anyone could bend to fit your lock, right? You wouldn’t

